Endpoint Security
Stop Cyber Threats before they Stop You. Elevate your security with intelligent, powerful, enterprise-grade endpoint security for all your devices.
Get Secure Today
Why is Endpoint Security More Than a Nice to Have?
As the world shifts to a remote or hybrid work model, more users are working from anywhere, from any device, than at any time in history, and attackers are quickly adjusting their tactics to take advantage of this change.
Businesses have been left weighing the benefits of enabling BYOD (allowing their end-users to access corporate resources that traditionally required VPN or on-premises access) against the increased risk of the same users unintentionally installing ransomware or other malware while performing non-work-related functions on their personal devices.
By enabling BYOD using a Zero Trust model, enterprises can reduce provisioning costs and avoid additional hardware purchases for work-from-home use, but they need to be able to protect their corporate assets on these devices, while still allowing the users to perform non-work functions on these same devices.
According to Microsoft Security Blog, 5 billion threats are detected on devices monthly
Every Layer of Your Business Deserves Protection
With a fully-fledged endpoint security solution in place, you can safeguard your organization against these security threats:
Identity
Devices
Applications
Documents
Even the most secure enterprises can be penetrated, but by the same token, even the most talented and resourceful hackers can be defeated. The way to do this is to put impediments in their way at every step.
At the endpoint, you do this by managing the device thoroughly from the beginning of the lifecycle, removing privileges not needed by the user, applying updates to all levels of software promptly, and encrypting data both in transit and at rest.
Microsoft Defender for Business gives you enterprise-grade level security for your business at an affordable cost.
Offered as a standalone solution or part of your Business Premium license, Microsoft Defender for Business solution is the next generation of security and protection your business needs.
Boost Your Endpoint Security with a Managed Service Provider
Mint UK as a Managed Services Provider delivers simple yet comprehensive endpoint security to help you secure your business, allowing you to focus on what matters.
You need a trusted expert to manage your security landscape after your initial deployment. By enlisting the services of an MSP, you can enable continuous security improvement through the following mechanisms:
Protect
Protect
Detect
Detect
Respond
Respond
A Modern Blueprint for Endpoint Protection
Are the security precautions you have in place today sufficient to stop cyber threats in your organization?

What Should Your Cybersecurity Framework Include?
STEP 1
The first step is to identify existing cyber touchpoints in your organization. Touchpoints are areas that could be at risk, including:
- IT assets
- Resources
- Data
STEP 2
Step 2 is to protect your touchpoints. This can be done through the following processes:
- Access security controls
- Data permissions
- Building an ongoing maintenance cybersecurity strategy.
STEP 3
Detection is done through consistent monitoring to identify any previous or potential breaches. Detection can be monitored at the following levels:
- Network
- Device
- Individuals
STEP 4
A response procedure will be developed to help guide your team to understand the threat lanscape and respond to threats quickly. A response plan includes the following:
- Understand breaches
- Fix vulnerabilities
- Implement strategies for recovery.
STEP 5
Disaster recovery systems are critical to business success. A recovery plan will detail:
- Backup procedures
- Communication frameworks to protect all stakeholders during a breach.
Overcome Your Security Challenges Today
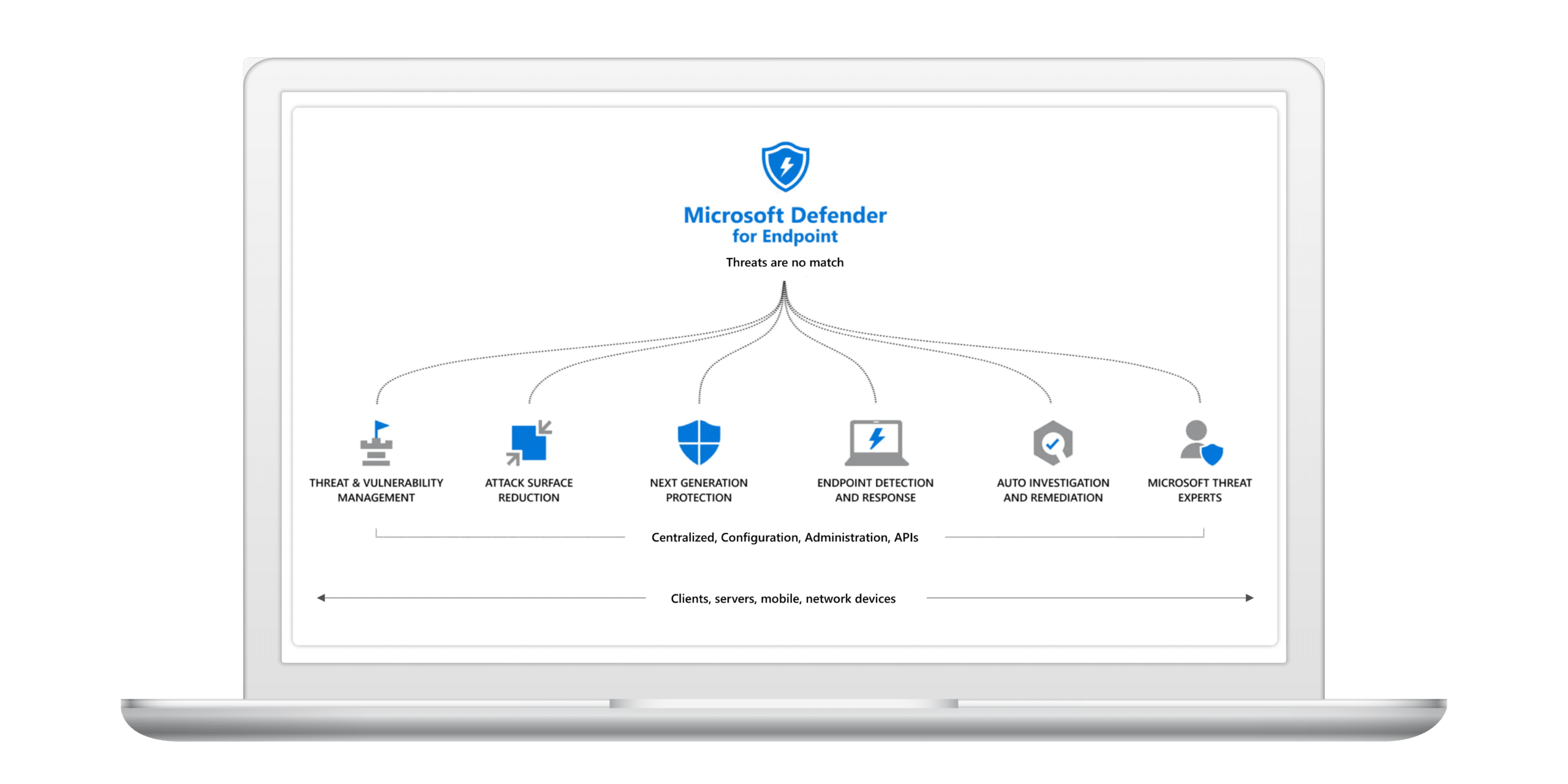
Threat and Vulnerability Management
Prioritize and focus on the weaknesses that pose the most urgent and the highest risk to your business. By discovering, prioritizing, and remediating software vulnerabilities and misconfigurations you can proactively build a secure foundation for your environment.
Attack Surface Reduction
Reduces your attack surface (places that your company is vulnerable to cyberattacks) across your devices and applications using capabilities such as ransomware mitigation, application control, web protection, network protection, network firewall, and attack surface reduction rules.
Next-Generation Protection
Helps to prevent and protect against threats at your front door with antimalware and antivirus protection—on your devices and in the cloud.
Endpoint detection and Response (EDR)
Get behavioral-based detection and response alerts allowing you to identify persistent threats and remove them from your environment. Manual response actions within Defender for Business will allow you to take action on processes and files, while live response will put you in direct control of a device to help ensure it’s remediated, secured, and ready to go.
API's and Integration
Automate workflows and integrate security data into your existing security platforms and reporting tools. For example, you can pull detections from Defender for Business into your security information and event management tool.
Why Choose Mint for EndPoint Security
Microsoft Defender For Business
Using Microsoft Defender for Business, you can build your security roadmap on a trusted platform, accelerated by Managed Services.
Customer Management at Scale
Monitor and manage customers in a personal manner, identify gaps in configuration, improve targets and drive adoption.
Proactive Risk Management
Realize efficiencies in customer management to support business scale and growth.
Improved Security Management
Ensure security and protection of your devices, people, and applications with a managed service provider.

SharePoint Intranets then vs. now: A UX Perspective

4 Things You Should Do Before Investing In A Teams Platform

Unveiling The Holy Grail Of Streamlined Productivity – O365
- Modern Work Partner of the Year 2021
- Content Services Charter Member 2021
- Advanced Specialisation Partner
